Security
Securing the Future of Enterprise AI: MongoDB and Mirror Security's VectaX
AI is revolutionizing how enterprises unlock insights, make decisions, and engage customers. In 2025 alone, over 60% of Fortune 500 firms have deployed AI-powered analytics or customer-assistants, yet high-profile incidents such as the "BankAI permissions leak" and multiple GDPR non-compliance fines show vulnerabilities persist.
How can leaders accelerate innovation without exposing sensitive data to risk or regulatory failure?
A Partnership Built for Compliance and Scale
Mirror Security partnered with MongoDB to address these exact challenges. MongoDB Atlas offers market-leading flexibility, encryption-at-rest, and extensive auditing. But securing in-use data, particularly AI embeddings, remains the hardest problem in enterprise AI security.
VectaX, Mirror Security's AI-native encryption and policy engine, solves this through Fully Homomorphic encryption, dynamic policy tags, and cryptographically enforced compliance. Together, they deliver a secure foundation for enterprise AI where data remains protected; policies are enforced automatically, and innovation never slows down.
Understanding MongoDB's Native Encryption Capabilities
MongoDB has made significant strides in encryption-in-use with its Queryable Encryption feature, which allows client-side encryption while still enabling queries on encrypted data. This represents an important step forward for securing traditional database workloads.
How MongoDB Queryable Encryption Works
MongoDB's Queryable Encryption uses a client-side Key Management System (KMS) approach where sensitive fields are encrypted before being sent to the database. The key capabilities include encrypting data client-side before storage, storing data as fully randomized ciphertext on the server, supporting queries on encrypted fields without server-side decryption, and integrating with enterprise KMS providers like AWS KMS, Azure Key Vault, and GCP Cloud KMS.
Supported Query Types and Limitations
MongoDB Queryable Encryption currently supports the following query types in production: equality queries ($eq, $ne, $in, $nin) and range queries ($lt, $lte, $gt, $gte). Additionally, prefix, suffix, and substring queries are available in public preview with MongoDB 8.2, though these are not yet production-ready.
However, there are important limitations that impact AI and vector database workloads:
Data Type Restrictions: Equality queries don't support double, decimal128, object, or array types—all commonly used in AI embeddings
No Vector/Embedding Support: Cannot perform similarity search on encrypted vector data—the core operation for AI retrieval systems
Single Query Type Per Field: Fields can be configured for either equality OR range queries, not both
No Array Document Encryption: Cannot encrypt fields within arrays of documents
Index Limitations: No support for TTL indexes or unique indexes on encrypted fields
Limited Aggregation Support: Many aggregation stages and expressions are unsupported against encrypted fields
Where VectaX Extends MongoDB's Capabilities
While MongoDB's Queryable Encryption excels traditional structured data protection, VectaX was purpose-built for the unique challenges of AI workloads. The critical gap is similarity search on encrypted data—the foundation of modern AI systems.
Fully Homomorphic Encryption for AI
VectaX uses advanced cryptographic techniques to perform mathematical operations on encrypted data. In the context of vector databases and AI memory, this enables semantic searches, queries, and other operations on fully encrypted data.
MongoDB's Queryable Encryption protects sensitive fields by keeping data encrypted throughout its lifecycle—in transit, at rest, and in use—while still supporting equality and range queries. However, it's designed for structured query patterns on discrete values. For AI use cases that require semantic understanding, similarity matching, and operations on high-dimensional embeddings, Mirror Vectax can complement MongoDB's capabilities.
Feature Comparison
Capability | MongoDB Queryable Encryption | Atlas + VectaX |
Encryption at Rest | ✓ | ✓ |
Structured Field Encryption | ✓ | ✓ |
Vector/Embedding Encryption | ✗ | ✓ |
Similarity Search on Ciphertext | ✗ | ✓ |
AI-Specific Policy Controls | ✗ | ✓ |
Array Field Encryption | Limited | ✓ |
Compliance Artifact Generation | Manual | Automated |
GDPR/HIPAA/SOC2 Ready | Partial | Turnkey |
Query Latency (10M vectors) | N/A (vectors unsupported) | ~121ms (~10% overhead) |
AI Embeddings: The Hidden Risk
AI systems drive support bots, knowledge bases, and analytics using vector databases. These systems store embeddings of mathematical representations of text, images, or audio that often encode confidential information, including contracts, customer data, and PII.
Without the right safeguards, a misconfigured similarity search could breach compliance boundaries or expose customer secrets. Regulations such as GDPR, HIPAA, and SOC 2 still apply, and security teams must ensure that even the most advanced AI systems meet those standards.
VectaX for MongoDB Atlas encrypts embeddings the moment they're created—never leaving them exposed in memory or disk. Queries run on ciphertext with enforced access policies, meeting GDPR, HIPAA, and SOC 2 requirements by default.
Integrated Architecture
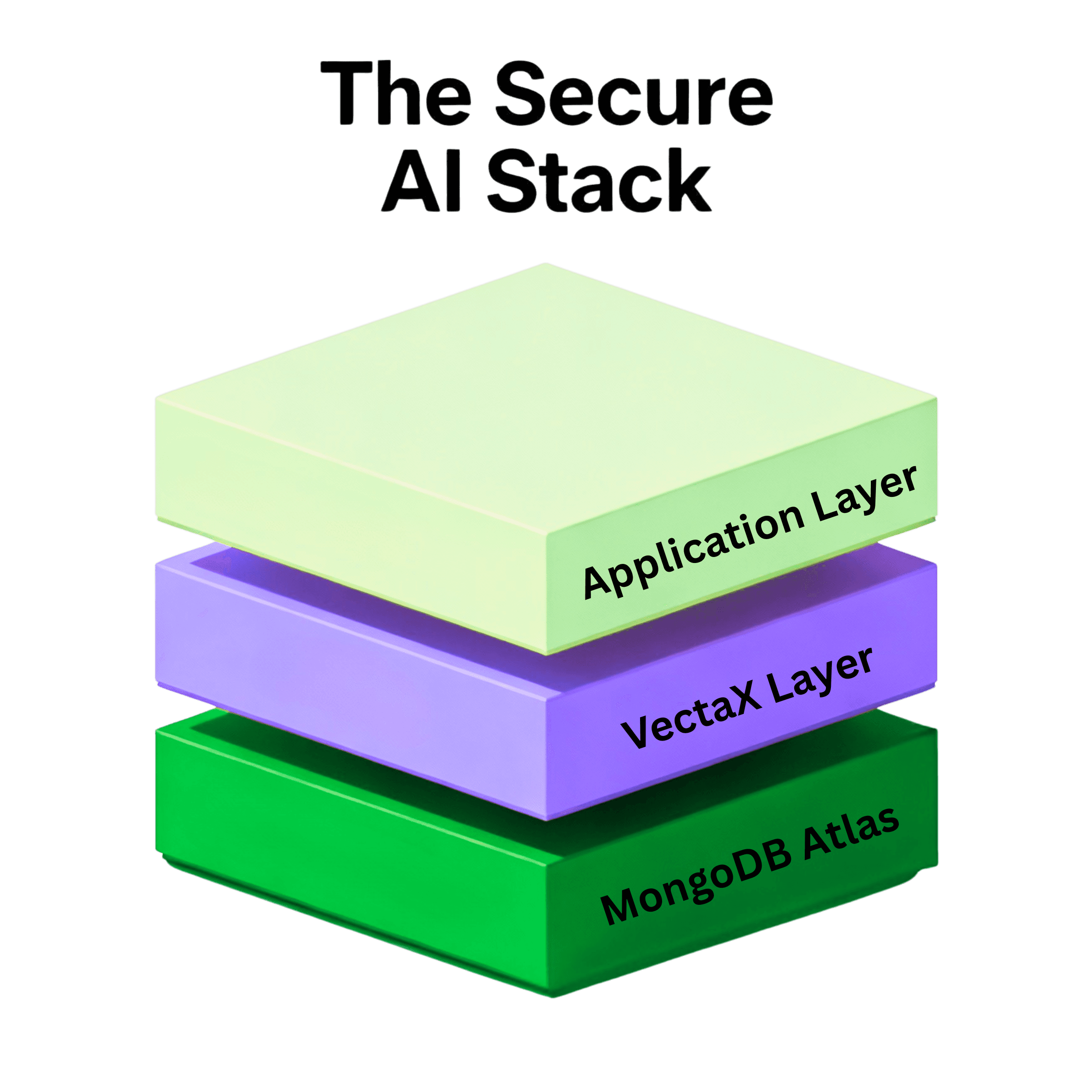
Application Layer: AI agent, support bot, retrieval system
VectaX Security Layer: Encryption engine, policy enforcement, audit logging
MongoDB Atlas: Vector search, encrypted data store, compliance controls
Process Flow: Encrypt → Validate → Search on Ciphertext → Filter Results → Decrypt → Return
Security for the CISO, Speed for the Developer
For Developers: Seamless Integration
Developers use MongoDB Atlas exactly as before; VectaX handles encryption and policy checks transparently. AI agents or retrieval applications issue queries, VectaX encrypts vectors and validates access policies, MongoDB performs the search, and results return securely filtered according to compliance requirements.
Internal testing showed minimal performance impact. Even at scale, the overhead remained near 10% while adding end-to-end encryption and auditable policy logs. As one engineer described it: "It just worked."
For CISOs: Cryptographic Proof of Compliance
VectaX provides real-time compliance posture and audit logs mapped directly to PCI-DSS, NIST, and SOC 2 controls:
Fully Homomorphic encryption: Enables secure vector search on ciphertext without decryption
AI-centric role-based access control: Dynamic, fine-grained controls tied to user, context, and workload
Real-time policy enforcement: Automated denial, logging, or escalation for queries breaching predefined boundaries
Compliance artifact generation: Direct output for audits and regulators
Preparing for What Comes Next
Both teams are expanding this collaboration to support new layers of protection:
Federated learning on encrypted data for multi-party AI training
Confidential computing for hardware-enforced in-use security
Cross-cloud vector synchronization with end-to-end encryption
Quantum-resilient encryption to prepare for next-generation computing risks
Insider incident detection powered by VectaX behavioral analytics
An Invitation to Build the Next Generation of Secure AI
Enterprises and developers can explore integration today. Mirror Security offers a sandbox environment where you can test secure vector search on MongoDB Atlas, experiment with real encryption and policy controls, generate compliance reports for your security team, and benchmark performance for your specific use case.
Organizations building large-scale AI systems can also join the beta program to collaborate on upcoming features and become anchor customers in the Secure AI initiative.
Ready to get started? Visit www.mirrorsecurity.io or contact the Mirror Security team directly.
Read more: Mirror Security’s Journey with MongoDB: Elevating Vector Security for Enterprise AI